Email Architecture, Gmail two Step Verification, SMTP POP3 IMAP
Table of Contents
Description:
Email Architecture, Gmail two Step Verification, SMTP POP3 IMAP- This article is going to be a little bit longer, as I will try to explain things in detail. We will discuss the Email Architecture, study the different protocols like SMTP “Simple Mail Transfer Protocol”, PoP3 “Post Office Protocol”, and IMAP “Internet Mail Access Protocol”. I will practically create a Gmail account, and then using the Gmail two step verification, I will practically demonstrate how to secure your Gmail account using a cell phone.
I will also explain why you need to activate the two step verification “2-step verification”. In this article I will also explain how to activate the most advanced security on your Gmail account so that the hackers can never hack your Gmail account. For the Gmail two factor authentication, we will be using the Yubikey Hardware Security Key invented by the Yubico.
Email Architecture:
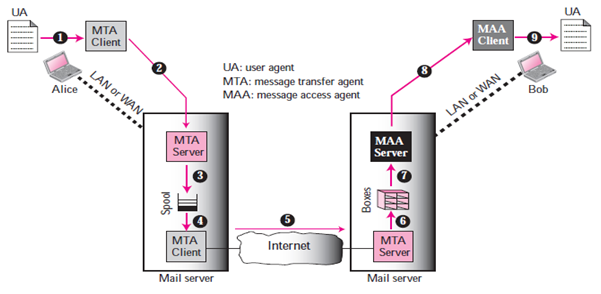
Email architecture consists of three components:
- User Agent (UA)
- Message Transfer Agent (MTA)
- Message Access Agent (MAA)
User Agent:
A user agent is a Package “or in simple words a program” of a software that composes, Reads, Responds to, and forward messages. It also handles user computers with local mailboxes.
Sending Mail:
In order to send a mail, the user creates mail through the UA which looks very similar to Postal Mail.
Receiving Mail:
The User agent, or a timer, is triggered by the User. Where a user has mail, the UA will notify the user with a notice if the user is ready to read the mail, a list will be shown in which each line includes a description of a particular message’s mailbox information.
Addresses:
A mail handling system must use a system address with unique addresses to deliver mails. Each user has a unique email address which is selected the time a person sign up for an email ID.
Mailing List or Group List:
Electronic mail allows for the one name, an alias, to represent several different email addresses; this is called a mailing list. The system checks the name of the recipient against the alias database whenever a message is to be sent; if there is a mailing list for the defined alias, separate messages, one for each entry in the list, must be prepared and given to the MTA.
Mail Transfer Agent “MTA”:
The actual mail transmission is done through MTAs. A system must have the client MTA for sending mail, and a system must have a server MTA for receiving mail. Simple Mail Transfer Protocol “SMTP” is the formal protocol that defines the MTA client and server within the internet.
Message Access Agent “MAA”:
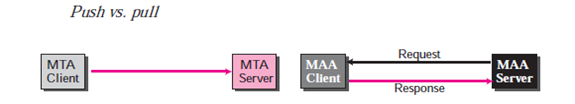
SMTP is used in the first and second phases of mail deliver. SMTP is not involved in the third stage, however, as SMTP is a push protocol; it transmits the client’s message to the server. The path of the bulk data “messages” is from client to server, in other words. On the other hand, a pull protocol is required to the third stage. The client must use the server to pull messages. The direction from the server to the client for the bulk data is the third stage that uses an agent for accessing messages. There are currently two protocols for accessing messages.
Post Office Protocol version 3 “POP3” and Internet Mail Access Protocol “IMAP”.
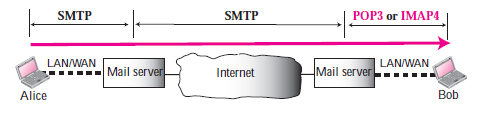
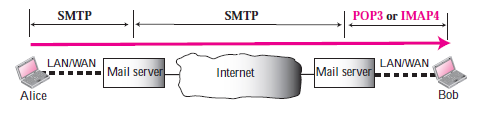
Simple Mail Transfer Protocol (SMTP):
SMTP is used two times, between the sender and the sender’s mail server and between the two mail servers. SMTP simply defines how commands and responses must be sent back and forth between an MTA client and an MTA server.
Commands:
Hello e.g. Electroniclinic.com
Send from e.g. engrfahad@wordpress-1263046-4550097.cloudwaysapps.com
Send to e.g. xyz@yahoo.com
Data: e.g. “Hope you are fine” etc
Response:
- Services Ready
- User not local; the message will be forwarded
- The command is not executed; mailbox unavailable etc.
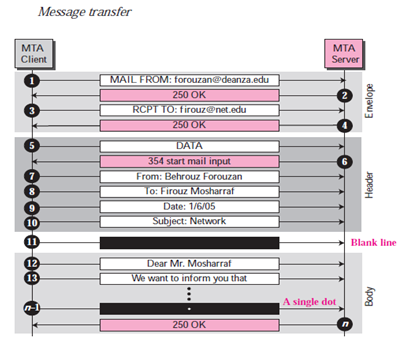
Mail Transfer Phases: The process of transmitting a mail message takes place in three phases: forming links, exchanging mail and terminating the connections.
Connection Establishment:
The SMTP server begins the connection process once a client has made a TCP link to the well-known port 25.
Mail Transfer:
 Connection Termination:
Connection Termination:
Upon successful transmission of the packet, the connection is terminated by the client. This is a two-stage process.
Message Access Agent Protocols: POP3 and IMAP4:
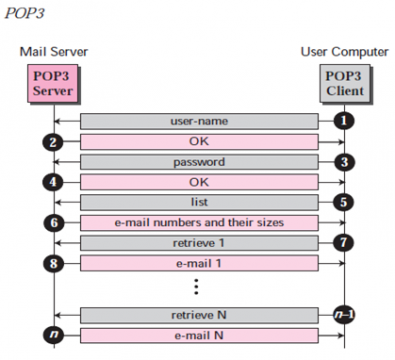
Version 3 (POP3) of the Post Office Protocol:
It is easy and functionally constrained. On the receiver computer the client POP3 software is installed; the server POP3 software is installed on the mail server. Mail access starts when the user has to retrieve his email from the mailbox on the mail server. On TCP port 110 the client opens a connection to the server. To enter the mailbox, It then sends the user name and password. The user will then, one by one, list and retrieve the emails.
Internet Mail Access Protocol, version 4 (IMAP4):
Another standard for accessing mail is the Internet Mail Access Standard, version 4 (IMAP4). IMAP4 is similar to POP3 but more features are available; IMAP4 is more powerful and more complex. There are several forms POP3 is deficient. It does not require the user to arrange their mail on the server; there are various directories on the server that the user can not. (Of course the user should build files on his own computer). However, POP3 does not allow the user to review the mail content partially before downloading. IMAP4 provides extra functions as follows:
- Before downloading a user can check the email header.
- Before downloading a user can search the email contents for a specific string of characters.
- Partially, a user can access email. This is particularly useful if the bandwidth is small and the email includes high bandwidth requirements for multimedia.
- A user on mail server can build, remove, or rename mailboxes.
- A user can construct a mailbox hierarchy in an email storage folder.
Multipurpose Internet Mail Extensions (MIME):
Electronic mail is structured simply. Yet its simplicity comes with a price. It can only send messages in 7-bit NVT ASCII format. It, in other words, has certain drawbacks. Languages other than English (such as French, German, Hebrew, Russian, Chinese, Urdu and Japanese) cannot be used. It may also not be used for sending binary files or video or audio data.
MIME is a supplementary protocol allowing the sending of non-ASCII data via email. At the sender location, MIME converts non-ASCII data into NVT ASCII data and transfers it to the MTA client to be sent over the Web. The message is converted back to the original data at the receiving site. MIME can be seen as a set of software functions that transform non-ASCII data into ASCII data, and vice versa
Web Mail, Web based Email:
Email is such a common application that some websites today provide this service to anyone who accesses the site. Three common sites are Hotmail, Yahoo, and Google. The idea is very simple. Let us go through two cases:
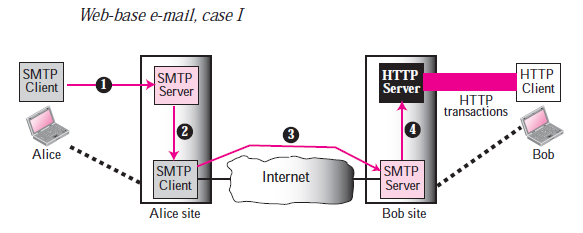
Case I
Alice, the sender, uses a conventional mail server in the first case; Bob, the recipient, has a Web based server account in it. Mail transfer is done via SMTP from Alice’s browser to their mail server. The message being transmitted from the sending mail server to the receiving mail server is still via SMTP. Nonetheless, the message to Bob’s browser from the receiving server (the web server) is done via HTTP. In other words, the HTTP is typically used instead of using POP3 or IMAP4. If Bob wants to get his emails recovered, he sends an HTTP request message to the website (for example, Hotmail).The website sends a form for Bob to fill in, which contains the user name and password. If the log-in name and password match, the e-mail list is transferred in HTML format from the Web server to Bob’s browser. Now Bob can browse through his received e-mails and then can get his e-mails one by one using more HTTP transactions.
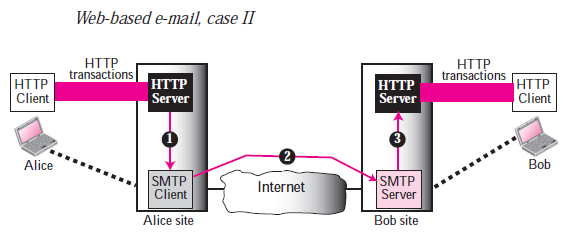
Case II:
Both Alice and Bob use Web servers in the second case but not exactly the same server. Using HTTP transfers Alice sends the message to the Web server. Alice sends an HTTP request message to its Web server using Bob’s mailbox name and address as the URL. The Alice server passes the message to the SMTP client and sends it via SMTP protocol to the server at the Bob site. Bob receives the message using transactions running HTTP. The communication from the server at the Alice site to the server at the Bob site, however, also happens using SMTP protocol.
I think we have covered enough theory, now let’s do some practical work. Now we will be creating a Gmail account and then we will secure the Gmail account using the two step verification “cell phone” and Hardware Security Key.
How to make a Gmail account:
Open any of your favorite Browser, I personally recommend Chrome, So, open a browser and search for Google.
Note: If you know how to create a Gmail account then you can skip this part.
You can start by typing Google sign up and press enter.
Click on the “create a Gmail account”
You will see a button captioned Create an Account simply click this button.
A form will be displayed, now fill this form and provide valid information, because this will help you in the future, if anything bad happens you can recover your Gmail account without any problem.
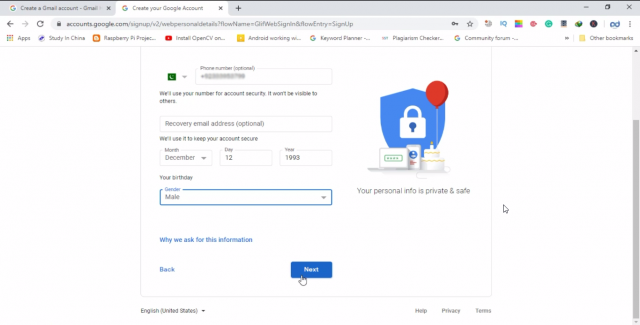
Then enter your cell phone date of birth and gender and click next, the information I am sharing right now is not correct as I am making this ID only for the demonstration purposes. Because I am not going to use this Gmail ID in the future.
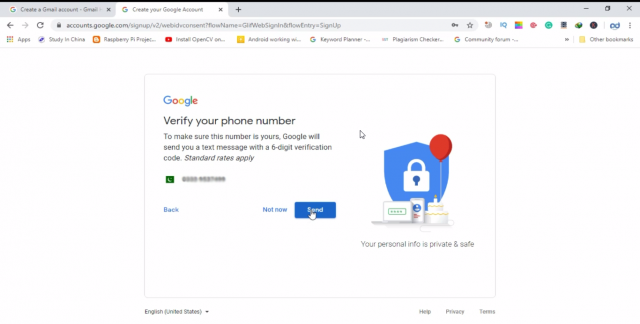
After you are done with the form fill up thing, you can click on the next button. This will take you to another page where you will need to verify your cell phone number.
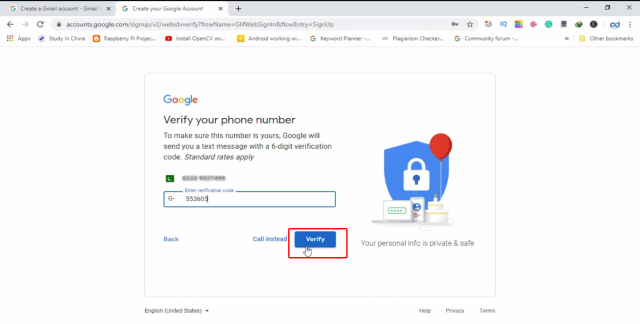
You will receive a verification code on your registered cell phone number, you will have to enter this number to verify.
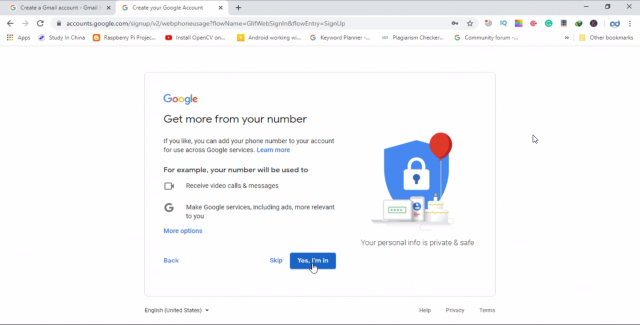
Then click on yes I’m in
The privacy and terms page will be opened, simply, click on I agree, if you have no problem with the Privacy and Terms or else you can cancel, this is totally up to you. But for the process to complete you have to press on I agree button. This is the final step.
So your account has been successfully created you will see welcome page
Now, you are all set. You can use this Gmail account for sending and receiving emails. If you are planning to use this Gmail ID for business purposes then I highly recommend to activate the Gmail two step verification, which is very simple. We have different types of 2-step verification, which we are going to discuss.
How to secure Gmail account / Gmail Security / Google Account Security:
As a beginner, you can first start with the Basic yet most commonly used two step verification which uses a cell phone. You can use your cell number to secure your Gmail account. Each time you log in to your Gmail account from a new device which can be a cell phone, computer, tablet, etc you will be asked to verify if it is really you. Google will send you a verification code, which you can manually enter. This sounds great? Ya, of course, but wait, it has advantages and disadvantages which you will know in a minute.
I myself used my cell phone number for the two step verification but, now I am not using this, I will tell you why I am not using this anymore. But as a beginner it’s super cool you can use your cell phone for the 2-step verification.
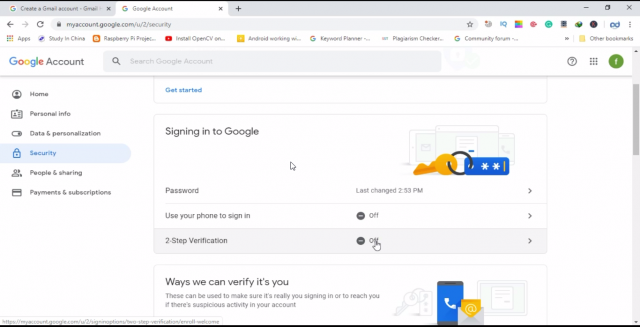
To make your Gmail account secure click on security
Then click on 2-step verification.
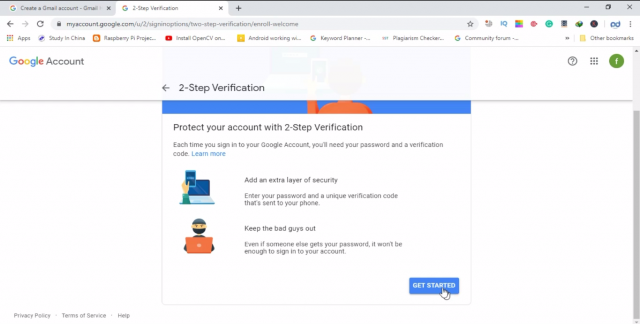
Click on get started
When you click on the get started it will ask you to enter your email ID and password, Google wants to make sure it is really you.
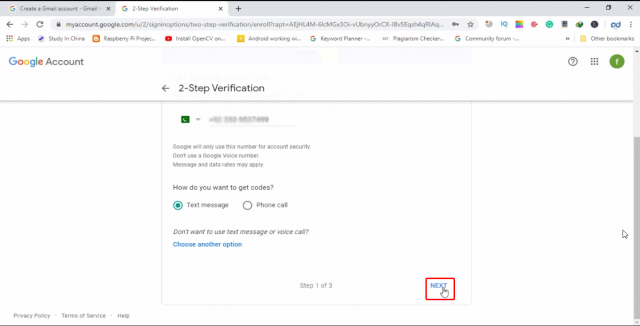
Enter your cell phone number, which you use on a regular basis because you will always need this number for verification. Make sure your cell phone is password protected. Because your cell phone is key to your Gmail account. Anyone can verify himself/herself as you.
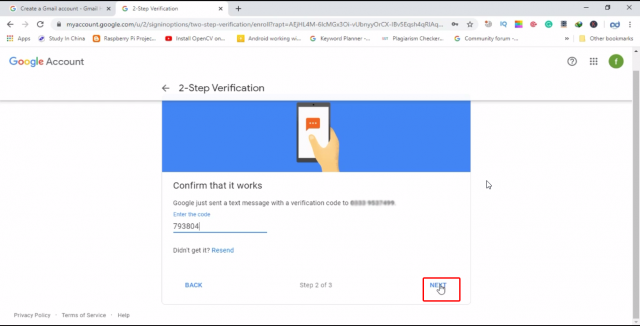
When you click on the Next button, you will get a verification code on your cell phone number, which you will have to enter for verification purposes. Enter the code and press next
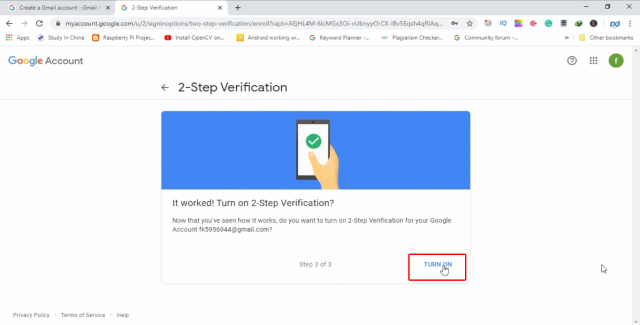
Then finally, turn on 2-step verification
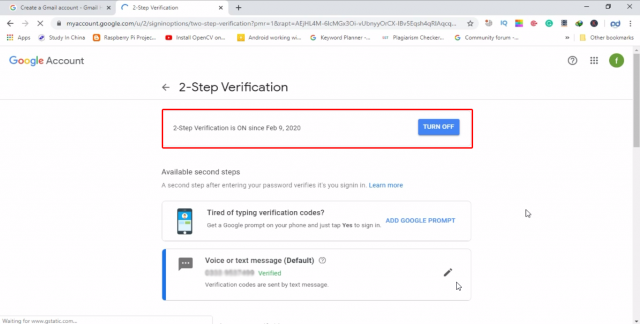
As you can see in the picture below the 2-step verification is on
Now, your Gmail two step verification process is completed. There is something that I want to share with you from my personal experience. I have been using Gmail accounts for years, for my YouTube channels and Google Adsense accounts. One day my cell phone stopped working and I was locked out of my Gmail account, as I was not able to verify the 2-step verification. So, the things which I am about to share with you, make sure you follow them.
While your Gmail two step verification is completed. Again log into your Gmail account, and open the security page, and click on the 2-step verification. Below your cell phone number you will see the backup codes. These codes can really make your life easier.
These printable one-time passcodes allow you to sign in when away from your phone, like when you are travelling, or your cell phone is damaged. When you click on the SET UP. The Google will give you 10 unique codes, each code you can use only one time. Make sure you keep these codes in a safe place but accessible. Let’s say your cell phone is damaged then you can use these codes to login into a new device.
If you are using your Gmail ID only for sending emails and not using them for Adsense accounts and YouTube channels then you can use your cell phone and backup codes without any tension.
But when it comes to the Paypal accounts, Amazon Affiliate accounts, YouTube Channels, Adsense Accounts then you cannot rely on only cell phone based two step verification and backup codes.
As you know, when you become popular, people have your PayPal account id, or let’s say you have a YouTube channel and have a lot of subscribers then hackers start trying to hack your Gmail accounts. You can search on the Google and find out how many YouTube channels and Facebook groups have been hacked. You know if someone know about your cell phone number, they can clone your number and then using that number they can easily take your YouTube channel or Adsense accounts. In the end, it will take a lot of time to reclaim your Gmail ID, or the hacker can delete all of your videos and information etc.
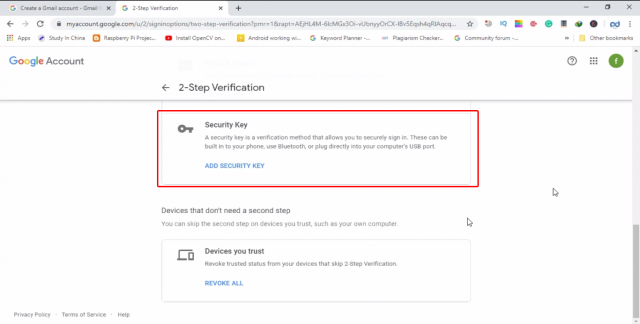
In such a case, then you should go for another 2-step verification, which I am personally using, it’s a hardware security based two step verification.
How to secure Gmail Account from Hackers:
How to secure Gmail from hacking? This is one of the most commonly asked questions. As I said earlier a lot of YouTube channels are hacked. Hackers can fool the beginners so easily, they know how to send fake emails. If you are running a YouTube channel, Facebook Group, Paypal account, Dropbox, Github, etc then I recommend you should use the Hardware security Key. The one I am using is Yubikey Hardware security key invented by the Yubico.
The security key is not for free, you will have to pay one time for the hardware key. But trust me it’s worth it. I have a complete video and article on this; which explains how to register multiple Hardware security keys. I highly recommend you should watch the following video and read the article. This will really help you in making your Gmail account Hack proof. I myself running a YouTube channel and, I am using the same thing for all of my channels, Facebook groups and all other online accounts.
Watch Video How to secure Gmail from hacking?
Detailed Article on Yubikey Hardware security key:
https://www.electroniclinic.com/yubikey-fido-u2f-security-key-by-yubico-secure-online-accounts/